The Leading Company in Penetration Testing, Application Security and Cloud Security

We offer highly reliable security testing solutions to clients, identifying potential vulnerabilities in their applications or products and safeguarding Sensitive data and business logic in these applications. We help clients understand, analyze, and act on security vulnerabilities in the correct context so that they do not face exploitation from any attackers.
Service Offerings
-
Our Approach
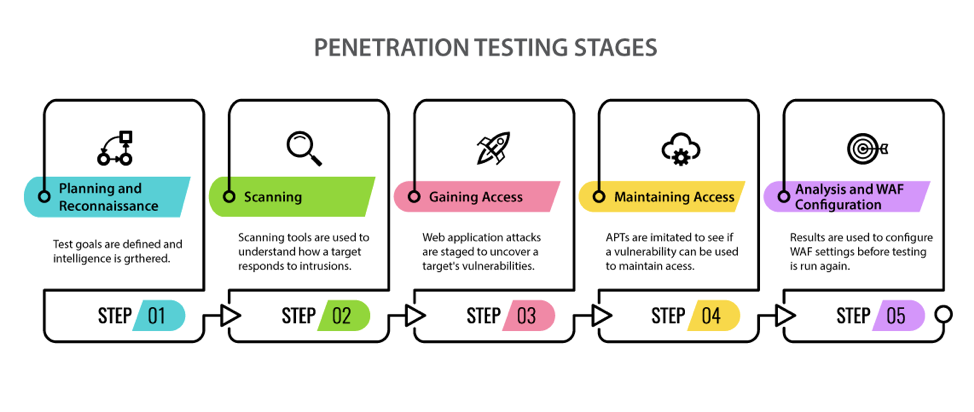
Penetration Testing constitutes that part of a security assessment exercise that attempts to simulate the techniques adopted by an attacker in compromising the target systems. Our penetration testing methodology is well lined up with established standards and practices, combined with our extensive experience.Types of Penetration Tests:
1. Web Application Security Testing
2. Network Penetration Testing -
Application Security Assessment
Application Security Risk Assessments are designed to identify and assess threats to the organization. Our application security assessment methodology is designed around the following well-known security assessment guides such as:
• OWASP Top 10 (Open Web Application Security Project)
• Threat Modeling processes such as STRIDE and DREAD
• OWASP’s Software Assurance Maturity Model (OpenSAMM)
• Open Security Testing Methodology Manual (OSTMM)
• Web Application Security Consortium (WASC) guidelines1. Dynamic Application Security Testing
2. Source Code Review
3. Threat Modelling -
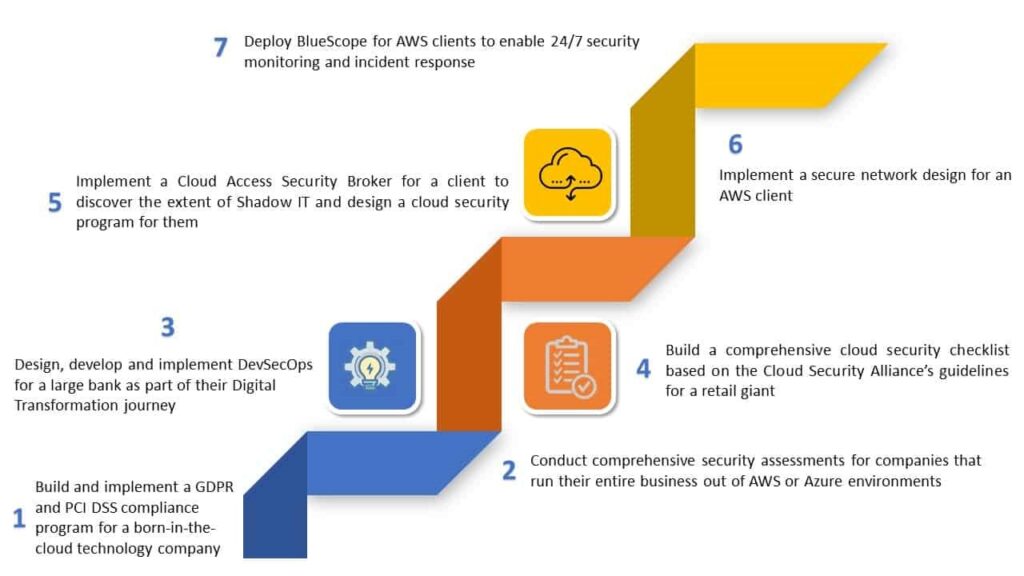
Assess
• Understand the current computing landscape of the organization and digital transformation roadmap.
• Analyze through the use of tools and interviews the extent of IT within the organization
• Understand the legal regulatory environment that impacts security and compliance requirements
Transform
• Create a cloud security policy that support the rules for cloud adoption by the business
• Redeem the policy highlighting the risks and benefits of cloud computing
• Create a cloud risk assessment framework for different cloud computing models (IaaS, PaaS, and SaaS)
• Design secure data transfer, cloud connectivity, and secure access solutions for cloud computing
• Implement security monitoring and continuous auditing mechanisms for cloud environments
Sustain
Implement a managed services security program that addresses the cloud computing environment of the client
• Continuous or periodic vulnerability assessments
• Continuous security monitoring and incident response
• Implementation of DevSecOps for application security
• Designing and implementing a cloud security metrics program
Tools we used